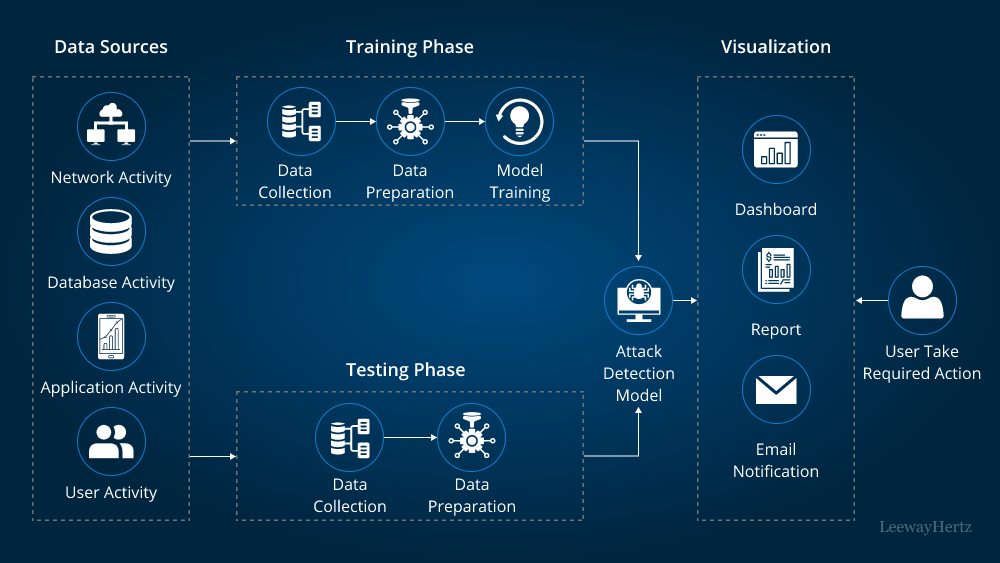
Cloud security solutions are rapidly transforming how organisations in Kuwait protect their critical data networks. As digital adoption surges across government, finance, oil and gas, healthcare and telecom sectors, ensuring networks are shielded from cyber threats has never been more essential. Through human centred design, these solutions not only secure data but also inspire confidence, agility, and peace of mind for Kuwaiti businesses and citizens.
Understanding Kuwait’s Data Threat Landscape
Kuwait’s digital infrastructure faces growing challenges: phishing, ransomware, insider threats, and nation state actors. With sensitive oil sector data and expanding e government services, a breach could cause severe financial and reputation damage. Cloud security solutions offer centralised protection that evolves with emerging risks, ensuring Kuwait’s networks remain resilient and trustworthy.
Key Elements of Cloud Security Solutions
Multi Layered Protection
Multi layered protection combines firewalls, intrusion detection, endpoint security, and data encryption. Each layer acts as a safety net should one barrier be breached, others remain in place. This holistic guard maintains data confidentiality, integrity, and availability.
Secure Identity and Access Management
Identity and access management (IAM) ensures only authorised users gain access. By implementing strong authentication, role based permissions, and regular audits, Kuwait’s institutions can prevent unauthorised access and reduce insider threat risks.
Real Time Threat Intelligence and Monitoring
Modern cloud security includes real time monitoring and threat intelligence. Continuous analysis of network activities helps detect anomalies immediately. Automated alerts and integrated response enable fast containment of threats before they escalate.

Data Encryption and Compliance Assurance
Encryption both at rest and in transit ensures data remains unreadable to unauthorised parties. In tandem, cloud solutions help organisations maintain compliance with Kuwait’s data regulations and global standards like ISO 27001 and GDPR, reinforcing trust among stakeholders.
Automated Incident Response
When a breach occurs, every second counts. Automated response tools isolate affected systems, block suspicious traffic, and notify administrators all within moments. This speed dramatically reduces damage and recovery times.
Scalable Cloud Infrastructure Security
Cloud environments must scale with demand. Elastic cloud resources, micro segmentation, and container security provide both flexibility and strong segmentation. This scalable approach ensures seamless performance without compromising protection.
Benefits for Kuwaiti Organizations
Strengthened Trust and Reputation
With cyber threats frequent and costly, robust cloud security builds confidence among citizens, partners, and international stakeholders. Kuwaiti businesses adopting strong protection are seen as reliable and forward thinking.
Operational Efficiency and Cost Savings
Centralised cloud security reduces the need for fragmented tools and manual oversight. Automated patrol, patching, and response lower operational burdens and allow IT teams to focus on strategic innovation.
Business Agility and Innovation
Secure cloud environments empower faster deployment of new digital services. Government agencies can roll out e services; banks can launch digital banking; healthcare providers can securely share patient data. All while maintaining robust defences.
Resilience Against Evolving Threats
Cyber threats are dynamic so must defences be. Cloud security platforms regularly update threat libraries, AI engines, and response protocols, ensuring Kuwait’s networks remain resilient to new attack types.
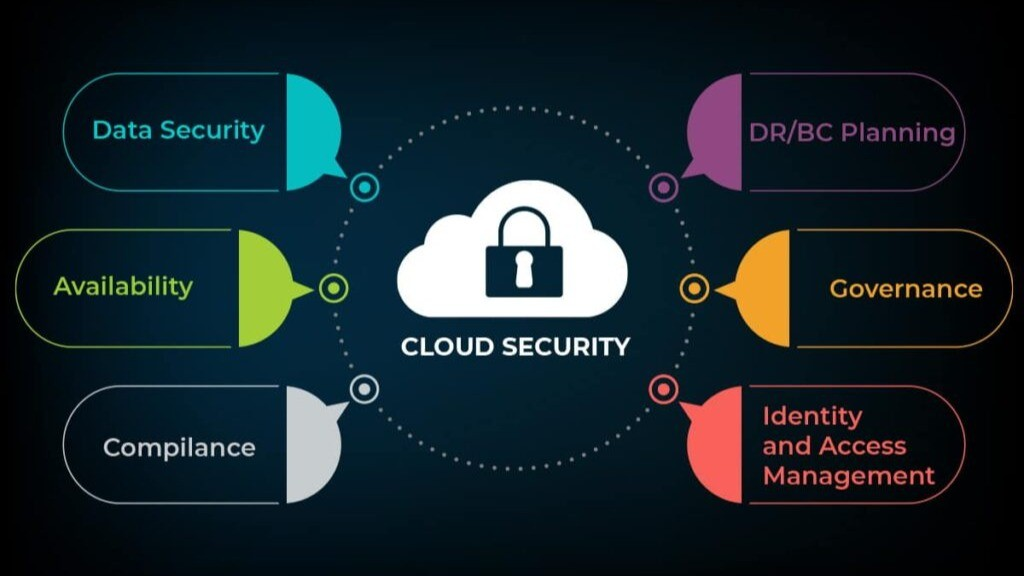
Adoption Strategies for Kuwait
Start with Risk Assessment
Organisations begin by mapping out data flows, identifying critical assets, and assessing vulnerabilities. Clear visibility into risk exposure informs what protections are crucial.
Choose Trusted Cloud Providers
Working with reputable cloud vendors that offer built in security controls like identity management, encryption, and monitoring can accelerate protection implementation while ensuring reliability.
Layer on Managed Security Services
Many Kuwaiti organisations benefit from partnering with managed security service providers (MSSPs). These experts provide dedicated monitoring, threat hunting, and incident support boosting protection without stretching internal teams.
Continuous Training and Awareness
Security is not just about technology it’s also about people. Regular employee training, phishing simulations, and awareness campaigns build a security first culture across the organisation.
Regular Audits and Updates
Security is a journey, not a destination. Periodic audits, penetration tests, and updates help ensure defenses remain strong as systems evolve and new threats emerge.
Inspiring Real World Use Cases
Government Digital Services
Kuwait’s government agencies are increasingly migrating services to secure cloud platforms issuing digital IDs, online licenses, and citizen portals with strong identity authentication and encryption to safeguard sensitive personal data.
Financial and Oil Sector Protection
Banks and energy companies store highly regulated data and operate mission critical systems. Cloud security solutions with encryption, IAM controls, and real time monitoring deliver operational continuity and regulatory compliance.
Healthcare Connectivity
Medical institutions are adopting cloud based health records and telemedicine. Secure access controls, encrypted transmissions, and continuous logging ensure patient privacy and smooth healthcare delivery.
Looking Ahead: The Future of Cloud Security in Kuwait
As Kuwait pursues its digital transformation vision, cloud security will serve as a foundational pillar. Emerging technologies such as AI driven threat detection, zero trust frameworks, and secure multi cloud orchestration will continue strengthening Kuwait’s resilience. By adopting these solutions, Kuwaiti organisations can confidently innovate while keeping data and networks secure.
Conclusion
Cloud security solutions offer powerful, positive transformation for Kuwait’s data networks fortifying operations, building trust, reducing cost, and enabling innovation. By embracing best practices risk assessment, trusted providers, managed services, continuous training, and regular updates organisations can navigate the cyber landscape with confidence and safeguard the digital future of Kuwait.
Do follow Gulf Magazine on Instagram.
Also Read – Gamification: Powerful Strategies Transforming Corporate Training in Kuwait